It doesn’t matter which operating system you use; you must utilize security software to keep your operating system or network secured. Basically, security programs are such utilities that serve you different purposes: removal of spyware, resistance to the virus, firewall protection, and many more.
In short, security tools can be referred to as the blood of an operating system that destroys harmful things like real blood. However there are numerous security programs, but all of those won’t function equally and properly with every operating system.
Hence, here we have listed the top 20 Linux security tools predominantly for Linux users, but you may also try them if you are a user of any other operating system.
Best Linux Security Tools
The security tools for Linux described below have been sorted out after lengthy research to provide you with the best one with authentic information. Each of the tools contains a general discussion with an impressive feature section to help you understand the potential of the tool in detail.
1. MISP
MISP, known as the “Malware Information Sharing Platform,” is a threat intellect platform to share, store, and correlate signs of threat intelligence, economic racket information, susceptibility information, and counter-violence information. This Linux security tool is useful for storing, sharing, collaborating cyber safety signs, malware exploration, and using the information and the IoCs to detect and prevent threats.
Important features
- Flexible enough to express complex objects and ally them together to reveal threat intelligence, occurrences, or linked elements.
- The “intuitive user interface” lets the end-users build, upgrade and cooperate on indicators/attributes and events.
- Stores facts in an organized layout with widespread cyber-security signs’ support.
- Combines signing and encryption of the warnings through PGP or/and MIME/S, considering your preferences.
2. Privacy Badger
It is basically a privacy safeguard for browsers that provides security against the trackers of a website visitor. The trackers normally gather information about your browser. The collected information is frequently shared by third parties. It is often used for creating a fake profile of a specific browser. In such a case, this Linux security tool hinders data collection.
Important features
- Runs as an extension on Opera, Firefox, and Chrome.
- Reviews the requested web pages and deactivate those by replacing the content or simply blocking the requests.
- Disables WebRTC that reveals the inner IP addresses.
- It helps you browse the net more securely.
- Requires a little space.
3. Aircrack-ng
It is an outstanding network application suite consisting of a packet, sniffer, detector, WPA/WPA2-PSK cracker, and WEP, and an analysis utility for ‘802.11’ wireless LANs. The software perfectly functions with any “wireless network interface controller” whose driver can nose 802.11g and 802.11a, 802.11b traffic and supports the raw observing mode.
Important features
- It runs under Windows, OS X, Linux, OpenBSD, and FreeBSD.
- Its packet can seize and export data to the text files for additional processing by the tools of the third party.
- Replays attacks, counterfeit access points, de-authentication, and other related things through packet injection.
- Checks the capabilities of the drivers and WiFi cards as well.
- Able to crack both WPA PSK and WEP.
4. Archery
Archery is a fabulous Linux security tool that helps you collect information regarding the vulnerabilities within your operating system. The software doesn’t only concentrate on authentic scanning but also allows the management of the findings in an essentially web-based interface. Here are the outstanding features of the utility:
Important features
- Comprises features such as dashboards, reporting, and searching.
- Can make interaction with other applications comprising the distinguished susceptibility scanners.
- Manages scans and susceptibility in CD/CI setting for DevOps teams.
- Its assessment and management of vulnerability are completely Open Source.
- Manages all the vulnerabilities of web-scan and discovers threats in your programs.
- Also manages all the network scans and discovers threats in the infrastructure.
5. Anchore
Anchore is a Linux security program that can help you detect, assess and authenticate the container images. You can store the images both in the cloud and on-premises. The tool mostly concentrates on the developers to successfully scrutinize the container images. Running inquiries and producing reports are the typical activities of Anchore.
Important features
- Inspects your container images and generates a complete list of config files, Java archives, etc.
- Integrates with instrumentation platforms to guarantee that your organization verifies the images run.
- Defines strategies to manage security susceptibilities, expose ports, manifest changes, etc.
6. ClamAV
ClamAV is a standard Linux security program for detecting mischievous programs or malware. Though ClamAV is known as an anti-virus engine, it perhaps will not come across numerous viruses because they are rare now. So, this software is expected to discover other types of malware, including ransomware, worms, and backdoors.
Important features
- You can use the tool in a number of techniques, from completing a random scan-up to scanning in a group.
- It doesn’t run ‘on-access scanning,’ but you can combine it with supplementary tools to obtain the same functionality.
- It can be adapted to assist in scanning incoming emails to detect malicious content.
- Supports numerous signature languages and file formats and unpacking of archives and files.
- Includes command-line utilities and a multi-threaded scanner daemon for instant scanning of files and update of signature automatically.
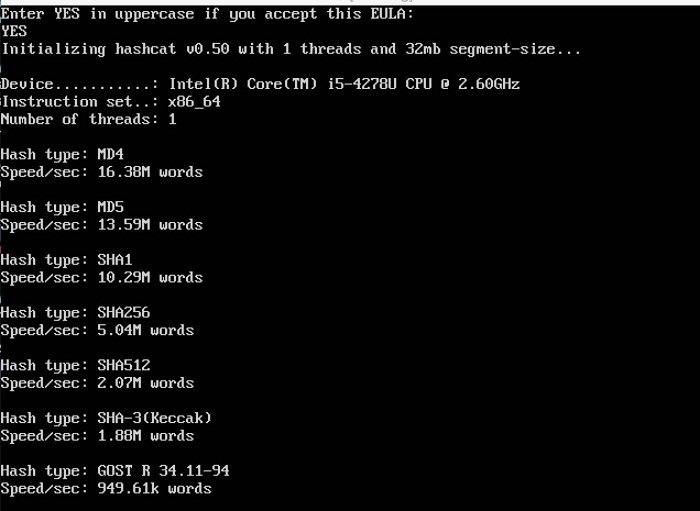
7. Hashchat
It is the self-declared world’s swiftest password retrieval tool with a copyrighted code-base until 2015, and now is a completely free program. Microsoft LM hashes, Cisco PIX, MD4, MySQL, MD5, Unix Crypt formats, and SHA-family are the basic instances of hashcat-supported hashing algorithms. The application comes both in GPU and CPU-based variants. Its editions are compatible with Windows, Linux, and OS X.
Important features
- Supports the brain functionality of a password candidate.
- Supports reading the password candidates both from stdin and file.
- Supports circulated cracking networks.
- Supports hex-charset and hex-salt.
- Supports automated keyspace ordering Markov chains.
- Contains an inbuilt benchmarking system.
- Supports automated tuning of performance.
8. radare2
Radare2 is one of the popular Linux security tools for performing “reverse engineering” on several dissimilar file types. You can use the tool to explore firmware, malware, or any other kind of ‘binary files.’ In addition to “reverse engineering,” you can even use it for forensics upon filesystems and data carving. With it, you can script the tasks as well. It is capable of using software exploitation functions in it.
Important features
- Supports various programming languages like JavaScript, Go, and Python.
- Uses influential analysis aptitudes for speeding up the reversing.
- Visualizes data configurations of a number of file types.
- Debugs with both local and distant debuggers.
- Patches applications to expose new and exciting features or repair susceptibilities.
- Disassembles several, unlike architectures.
9. Buttercup for desktop
No, it’s not the name of any delicious dessert we will present to convince you to eat. Instead, it is a mind-blowing password manager intended to help you control your credentials. Powerful encryption guards your sensitive files and materials under only one master password.
Important features
- Allows you to use more difficult passwords for individual services and stores those securely.
- You can install it directly on Google Chrome, while on Mozilla Firefox, the tool is found as an extension.
- Includes simple to-use interface where saving and finding the details of login is easier.
- Completely free to use on all the key platforms.
- Serves equally both on Android and Ios mobile phones.
10. Bro
“Bro” helps you extensively perform the monitoring of security, looking into the activities of the network. This Linux security utility can identify doubtful data streams. Considering the data, the program alerts, reacts and even integrates with other related tools. This fabulous software has been advanced by Vern Paxson, who now leads the project with a potential group of scholars and developers.
Important features
- Its domain-based scripting language facilitates site-specific observing strategies.
- It aims at high-performance networks.
- Not bound to any specific discovery tactic and doesn’t depend on outdated signatures.
- Expansively records what it finds and offers a high-level store of the activities of a network.
- Interfaces with other programs for the give-and-take of information in real time.
- Maintains far-reaching program-layer state regarding the network it observes.
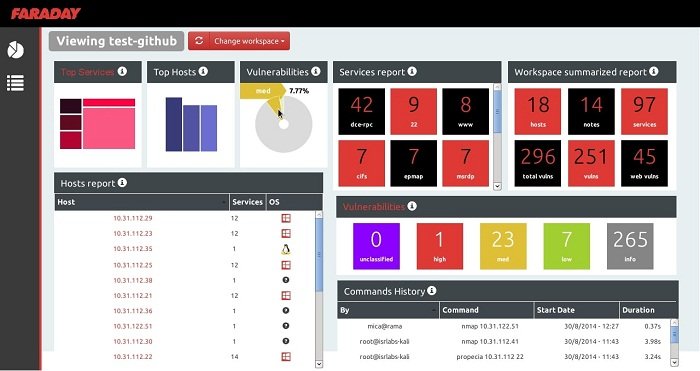
11. Faraday
Faraday is a real-time cooperative utility that upsurges velocity, efficiency, and transparency for your and your teams’ assessments. This Linux security tool provides you with superior perceptibility and helps make cooler safekeeping investments. The software serves many organizations all over the world. It can even meet the requirements of different organizations offering appropriate solutions to each case.
Important features
- Equipped with simplicity with a particular set of functional activities that help you develop accomplishing your work.
- As a user, you have the opportunity to generate a timeline that contains each historical modification within the existing penetration investigation.
- It allows making a comparison of two, unlike pentests.
- Enables the corporates, penetration testers, and project managers to have a real-time view of the work in development.
12. Frida
Another great Linux security framework- “Frida” lets the researchers and developers inoculate ‘custom scripts’ into ‘black box methods.’ This way, the tool provides all the functions with a hook, letting you trace the performed instructions. It even approves uninterrupted manipulation and observes the outcomes.
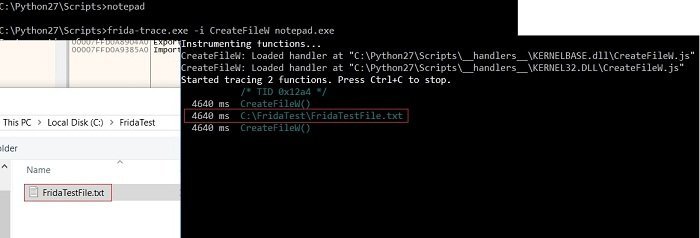
Important features
- You can get Frida with available bindings for various programming languages relating to processes.
- It doesn’t require any source code for tracing personal application code and hooking functions.
- Allows you to edit, store, and examine the outcomes.
- Contains a complete test suite.
- Available options for personalization and addition.
- Compatible with QNX, Windows, GNU/Linux, Android, macOS, and iOS.
13. PTF
PTF, the short form of “PenTesters Framework,” is a Python script that aims at keeping your penetration analysis toolkit the latest. It is an excellent Linux security program intended to run under Ubuntu, Arch Linux, Debian, or associated clones. It functions with modules where you get the definition of the method of fetching a tool and an overview of the needed things for building the tool.
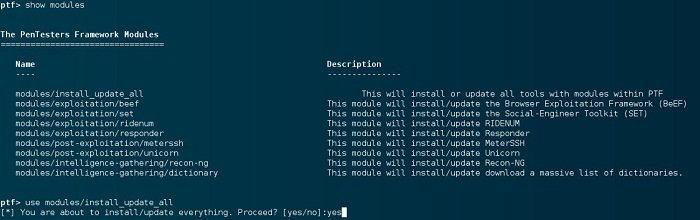
Important features
- Capable of retrieving, compiling, and installing the tools normally used by you.
- The tool is a modular structure; you can utilize lots of typical pen-testing tools and attach your own utilities.
- Makes sure that each and everything is structured according to the “Penetration Testing Execution Standard.”
14. Intrigue
It is one of the finest Linux security utilities extensively used to discover the attack surface. The discovery relates to applications and infrastructure, vulnerability, and security research.
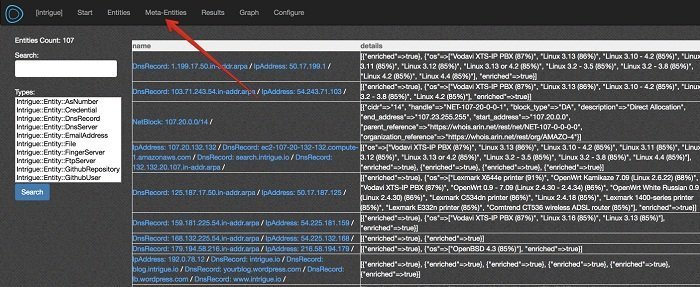
Important features
- Includes a bunch of scripts to sort out the required information.
- Provides unmatched visibility of external assets.
- Identifies the uncovered susceptibilities in the program stacks and their core hosts.
- Let you export vulnerability information for the management teams.
- It helps the security teams gain perceptibility of the third-party risk.
- Allows you to enrich the existing data and carry out OSINT exploration.
- Enables security teams to identify the unused assets that still pose a threat to the company.
15. Vault
It is a fantastic secret management program made by HashiCorp that is an expert in preserving your invaluable data. The secrets stored by it are normally utilized by software scripts and components. Vault employs an API to let you have access to the encoded secrets. The confidential issues themselves can either be prevalent or dynamically created.
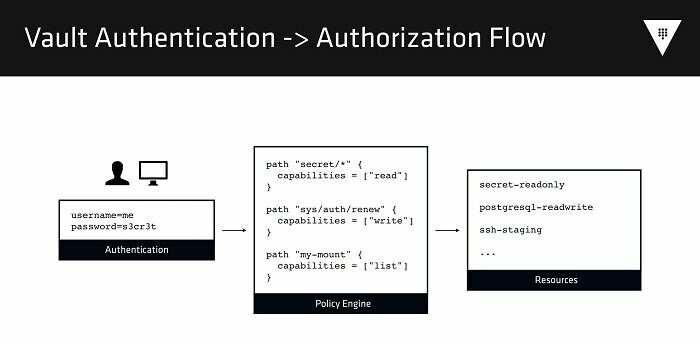
Important features
- Allows storing confidential things, including STS/ AWS IAM credentials, value/key pairs, NoSQL/ SQL databases, SSH credentials, X.509 certificates, and other sensitive details.
- Includes leasing, auditing, key rolling, and key revocation.
- It offers encryption just like a service with ‘integrated key management.’
- Simplifies the encryption of data both at rest and in transit across data centers and clouds.
16. CAIRIS
CAIRIS, an outstanding Linux security framework, stands for “Computer Aided Integration of Requirements and Information Security.” It is a great platform to elicit, specify, and validate the functioning systems. The tool was created to support each element required to analyze risk, usability, and requirements.
Important features
- Allows you to create a safeguard for software and designing of the system.
- It lets you track the communications between data points, objects, and associated risks.
- Automatically generates threat models like “Data Flow Diagrams” as soon as your design of the primary phase evolves.
- Produces a series of papers from “Volere compliant requirement specifications” to “GDPR DPIA documents.”
- Leverages open source brain about probable attacks and candidate safeguard architectures for measuring the attack surface.
17. O-Saft
It is one of those rare command-line tools that you can use both in closed settings and offline. The Linux security application contains a Tk/Tcl-based graphical user interface. Besides, you can turn it into an online CGI utility.
Important features
- Provides convenient SSL configuration information with its elementary parameters.
- Performs more particular tests with limited tool tuning.
- Allows you to gather information, test penetration, assess security, scan vulnerability, or analyze web applications.
- Supports STARTTLS for different protocols, including SMTP, IRC, POP3, XMPP, IMAP, RDP, and LDAP.
- Checks for securities against attacks such as BEAST, FREAK, DROWN, CRIME, etc.
- Shows the details of the certificate and SSL connection.
18. YARA
YARA is another fabulous Linux security utility intended to assist malware scholars in recognizing and categorizing malware samples without any limitations. With this framework, you can easily produce descriptions of the malware families or anything else according to your desire grounded on binary or textual patterns. All the descriptions, also known as rules, consist of a boolean expression and many strings.
Important features
- It lets you create more compound and influential rules using case-insensitive strings, wild cards, special operators, regular expressions, and other features.
- Equally runs on Linux, Mac OS X, and Windows.
- You can use it from your personal “Python scripts” with an extension of Yara-python or via YARA’s command-line interface.
19. OpenSSL
This is a marvelous software library suitable for your applications to protect interactions over the computer networks against overhearing. The central library is written using the C programming language. This Linux security utility is extensively adopted in the web servers of the Internet, and now most of the websites are served by it.
Important features
- Includes an open source execution of the TLS and SSL protocols.
- The core library can execute fundamental cryptographic tasks and provide different tool functions.
- Wrappers allow you to use the OpenSSL library with multiple computer languages.
- Editions are compatible with Windows, OpenVMS, and most Unix and Unix-like operating systems, including Linux, Solaris, QNX, macOS, etc.
20. Confidant
Confidant, popularly known as “storage of secrets,” provides a substitute by preserving confidential facts in a database instead of a configuration file. The tool functions so that it doesn’t give access to all applications to have the facts. Even often, the system managers are not given access if anything dubious is captured by Confidant.
Important features
- Solves the verification egg and chicken problem using IAM and AWS KMS.
- Stores your confidential files in an append-only method creating an exclusive KMS data key for the revisions of all the secrets.
- Provides an “AngularJS web interface” that lets the end-users manage the secrets and their mappings very easily.
Concluding Words
So, this is all about the “Linux Security Tools.” We hope this software and tools compilation will help you set up a secured OS. However, please let us know your opinion regarding our writing through a comment below to know your expectations from us and act accordingly next time. And yes, most importantly, don’t forget to share the writing to escalate our inspiration needed to bring betterment.

Congratulations Mehedi! I learnt a lot from your post. I started using Ubuntu in 2008 and I love Linux.