The internet has transformed the world into a microcosm, which offers camaraderie through sharing information and values. Global cognitive norm is getting evaded regarding the data being spied on, which implies that internet security is at stake. Chameleon sources are tremendously cynical; hence, the free flow of information is getting impeded significantly. A continuing threat of hacking and spying proliferation has triggered the alarm to encrypt data to protect it from the brute-attacker. To this end, plenty of files and disk encryption software could be used on the Linux platform; thus, information and data would have had to be protected from the brute-attacker. If you are a Windows user, then we have covered another article on Best Encryption Software For Windows. You can have a look.
Disk and File Encryption Software for Linux
Encryption is a process that converts plain text to a code number that is merely readable by authorized people. Again, it would be understandable to the typical users only if it is decrypted.
Having encrypted the data with the disk or file encryption software, all electronic devices, namely laptops and computers, can be secured thoroughly. Besides, in this competitive age, the rivalry is everywhere.
Organizations and companies try to collect information in different ways to take the competitive edge that eventually might lead to malpractice. There are many handy disk and file encryption software on the Linux platform to prevent data from being stolen from the laptop and computer. All of those have been discussed in the following.
1. EncFS
EncFS is a plausible and tremendously user-friendly file encryption software that would be used on the Linux platform. It works in a particular way, i.e., data get stored in the rootdir directory through a virtual file system.
Moreover, the mount point list makes the data available to visualize the unencrypted data to the users. Also, a password must be supplied to encrypt the file contents and the file names simultaneously.
For instance, the EncFS performs distinctly; if at a specific rootdir directory it cannot track the supported file system, it will pop up a suggestion to generate a new file system at the particular file space. Furthermore, a couple of options will be floated for the users to grip to some extent of control over the used algorithm.
Features of EncFS
- FUSE is used to collaborate between an encrypted directory and another specified directory.
- The Loopback system is not being used like other competitive systems.
- Root privileges do not necessarily require implementing this file encryption tool; thus, the users can use encrypted repository files.
- Without modification, it can work on existing file systems; hence, users do not require generating any file or even a file system within it.
2. TOMB
Tomb is recognized as one of the best file encryption software for the Linux platform available in open sources and facilitates preserving secret files. Having been written with code, it boons easy review and promotes links with commonly shared components.
Its authentic system generates encrypted storage files that could be closed or opened by applying its associated essential files, which are even protected with the user’s chosen passwords.
Tomb is safe and secured file encryption software on the Linux platform that could be protected and transported with a file system since keys can be kept in a discrete file, as an illustration; tomb files can store in the computer hard disc, whereas keys would be preserved on a portable USB stick.
Features of TOMB
- Tomb file encryption tool is designed with a simple shell script that can be downloaded for FREE.
- It requires root access as it works from the core terminal command line.
- It facilitates sound function, e.g., its software and key can be stored in physically distinct files.
- It has been written with readable codes, is user-friendly, and functions with the well-tested standard.
3. VeraCrypt
VeraCrypt is a free disk encryption tool that is effectively handy for the Linux platform. It is being branded the upgraded version of the TrueCrypt. The algorithms used for the system are significantly protected because of their enhanced security integration.
Moreover, its discrete encrypted wall impasses the barbarian invasion from spies and hackers. Its minor drawback is; it delays opening the encrypted partitions since it is developed with the integrated enhanced security program.
Nevertheless, it eventually boons the legitimate authority to access the computer, whereas it impedes the attacker effectively. It is an open source free disk encryption software for the Linux platform that can be downloaded very easily.
Features of VeraCrypt
- VeraCrypt facilitates the natural formation of a virtual disk that can allow encrypting the whole storage device.
- Real-time full encryption is supported automatically implies that; data would stay protected even without users’ command.
- VeraCrypt disk encryption tool boosts security for the computer to a greater extent.
- Having added a downloadable installer, generic Linux platform users can install it again and again.
4. TrueCrypt
Besides, TruCrypt is; on top of another free, open-source disk encryption software for the Linux platform that provides credible security for the users. Overwhelmingly, it works distinctly, i.e., it spawns in a file encrypted disc that functions as a mounted disc.
It encrypts all the files’ contents and integrates the directory’s name. Furthermore, having been encrypted, there is no scope to look into the files, HDD, and partitions.
This disk encryption tool can generate a specific size of individual files that the users can safely use. However, it is worth mentioning here that TrueCrypt has stopped producing a new version of the software; nevertheless; still, it can be downloaded from open sources for free for the Linux platform.
Features of TrueCrypt
- It generates a form of the virtual encrypted disk in a file that facilitates a real disk.
- A laptop can encrypt the whole storage and partition, for instance, a hard drive or USB flash drive.
- TrueCrypt disk encryption software automatically and transparently can encrypt the entire drive and function on the fly.
- In an adverse circumstance, it promptly impasses the access by precipitating two layers of a barrier.
5. Cryptmount
Cryptmount is a higher-end user-friendly file encryption tool for the Linux platform that enables users to encrypt a specific filing system. It does not require superuser privileges.
Moreover, it significantly allows the superuser to generate an entirely new encrypted file system. While the system administrator paves the way to configuring the initial filing system, a user needs to provide the decryption password for that filing system.
It clears the way for cryptmount to configure the device-mapper automatically. The devmapper mechanism has been used to develop this software that prompts frequent users to access the encrypted file filesystem when needed.
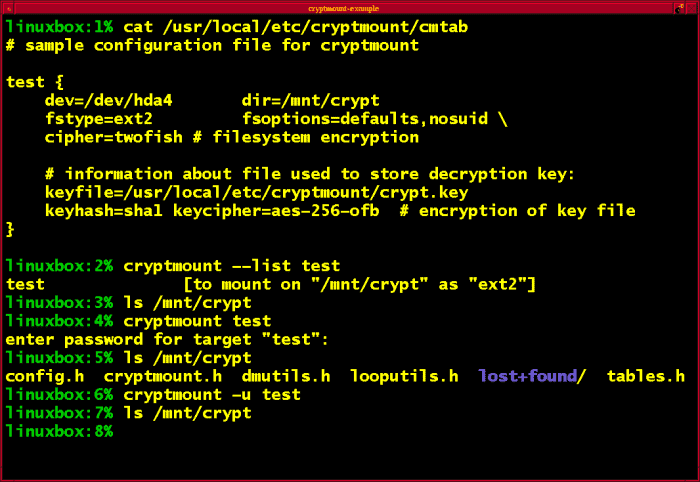
Features of Cryptmount
- It supplies a basic interactive setup script to encrypt the filesystem effectively.
- It can create the required filesystem without the superuser or administrator privileges that enable the typical user to access the data.
- This file encryption software facilitates generating more than one encrypted filesystem in a single disc partition supported and would be configured automatically in the system boot up.
- The encrypted filesystem is kept in an open format and handled with the human hand regarding the configuration information.
6. CryFS
It is an open source, one of the best file encryption software for the Linux platform that can be used only for the file contents. Moreover, it has been designed for metadata, directory structure confidentiality, and file sizes.
It creates the same size contents file blocks and encrypts the whole block simultaneously and individually. The base directory is used to store all the encrypted files where a random ID is applied as the file name.
The synchronized base directory is then set up to be connected with a cloud provider, for instance, Dropbox. In case of an attack, the base directory can be seen; however, metadata, file size, and directory structure of data will not be visible.
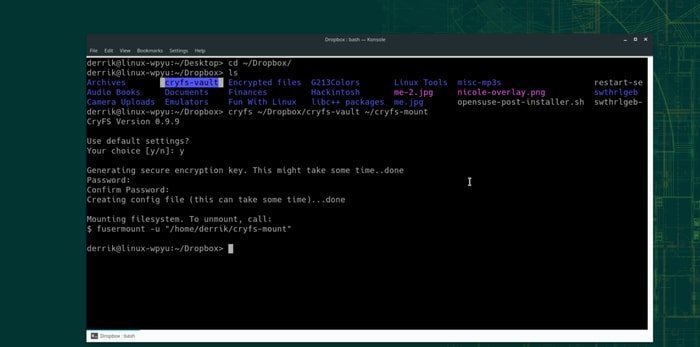
Feature of CryFS
- A configuration file is contained in the file directory along with the information CryFS requires to decrypt it.
- The encrypted files are protected with this configuration since users chosen passwords are applied; furthermore, integrity checks get done.
- The configuration files get encrypted twice, i.e., once by using aes-256-gcm and again with the surer chosen password.
- Additionally, the CryFS file encryption tool prompts inner and outer keys that impasse attackers very effectively.
7. GnuPG
GnuPG could be elaborated as GNU Privacy Guard, also known as GPG. Like most other disk encryption tools, it is an open source software that offers open GPG standards for the users.
The Linux platform uses this tool to encrypt and decrypt files from the command line. On an internet platform where data is most vulnerable, this disk encryption software lets users encrypt the data to protect it and ensure secure electronic communication.
GnuPG paves the way for a chameleon key management system to access modules for different sorts of public key directories. However, it can be easily integrated with various other applications of computers on the Linux platform.
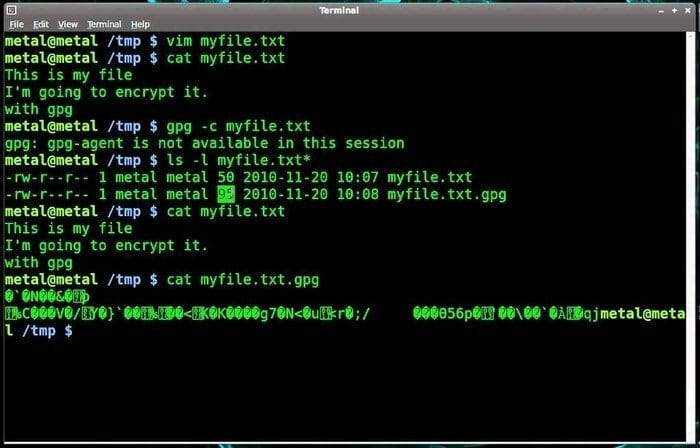
Features of GnuPG
- It is hybrid bets disk encryption software that is compiled with conventional symmetric-key cryptography and public-key cryptography.
- Asymmetric key pairs are used to generate individually to encrypt messages by the users.
- The GnuPG also supports symmetric encryption algorithms to a greater extent on the Linux platform.
8. 7-zip
7-zip is a file encryption utility tool that is free and available in the open source and can be used to insert a high number of files in a compressed mode, what is called an archive. Igor Pavlov developed this encryption tool, and it was first published in 1999.
This file encryption tool uses its 7z archive; it can read and write different archive formats. A command-line interface is used in this program as a command, and a graphical user interface characterizes the shell integration.
Apart from its format, it also works with some other compressed or non-compressed formats, such as ZIP, Gzip, bzip2, xz, tar, and WIM. Additionally, this encryption tool is also used for unpacking NTFS, SquashFS, UDF, FAT, HFS, ISO, MBR, VHD disk images, and so on.
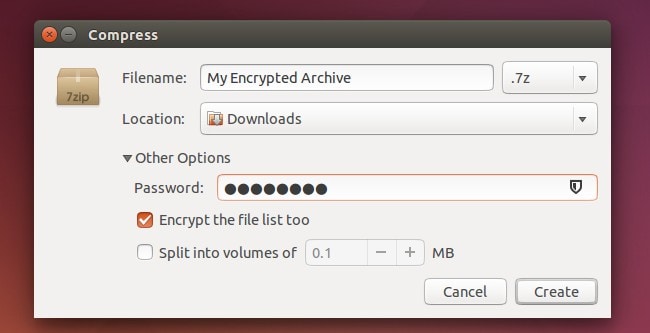
Features of 7-zip
- By default, 7-zip file encryption software generates a 7z archive format with a .7z file extension where archives can contain multiple directories and files.
- A Variety of algorithms are used for the core 7z compression, where bzip2, PPMd, and LZMA2 are the most common.
- The original 7z file format is modular and open and stored as Unicode.
9. dm-crypt
Arguably, dm-crypt is a transparent disk encryption tool subsystem for Linux kernel and in Dragonfly BSD. Being part of the device-mapper infrastructure, a cryptographic routine is used from the kernel’s crypto API.
Dm-crypt was programmed to underpin the advanced operation format, for instance, XTS, LRW, and ESSIV, to impure the shadow attack. What is more, it addresses a few reliability issues of cryptoloop.
This dm-crypt device-mapper target is stored in the in-kernel space; additionally, it works to encrypt the block device. However, it necessarily does not transform any data itself.
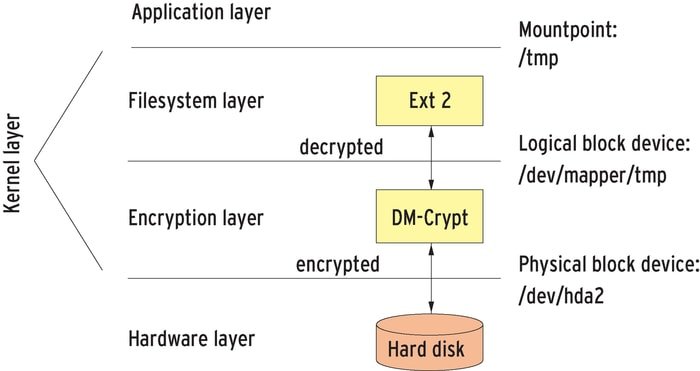
Features of dm-crypt
- This tool only works for the transparent encryption of virtual block devices, allowing it a large amount of flexibility.
- It also could be configured to pave the way for pre-boot authentication by an initrd to facilitate encrypting entire data on a computer.
- This disk encryption software is also vulnerable to watermarking attacks, while cipher block chaining is used with other disk encryption software.
10. eCryptfs
eCryptfs is an all-square-free and open source disk encryption tool on the Linux platform that works from the POSIX filesystem-level encryption stage to expedite a similar sort of function like GnuPG from the core operating system layer.
Moreover, it has been part of the Linux kernel since the updated version 2.6.19. It has been taken from Erez Zadok’s cryptfs that prompt different functions in open PGP file format to encrypt data.
Additionally, it smoothes the way for accessing random data from storing cryptography, along with the distinct file. Moreover, files and directories names get encrypted, which are typically large.

Features of eCrypts
- This disk encryption software works at a Linux kernel runtime in an interactive way where an ecryptfs envisage mounting an encrypted directory towards another unencrypted mount point.
- An encrypted directory would be shared with the tool between the users; nevertheless, encryption will be linked with a passphrase, which would be shared.
- Documentations are made by using a significant number of acronyms.
- The encrypted directory is defined as a lower, and the unencrypted directory as an upper.
11. Cryptsetup
On the Linux platform, Cryptsetup file encryption software plays a vital role as a command tool to confederate with the dm-crypt for accessing, creating, and managing encrypted devices.
At a later stage, it can be expanded to assist the various encryption types that are dependent on the cryptographic module and the Linux kernel device-mapper.
It is worth mentioning here; Linux Unified Key Setup (LUKS) expansion where required setup information is stored on the disk itself.
The purpose of this setup is to envisage smooth, seamless usage through virtual partitions and critical management. When devices are excessed through device-mapper, they are called block devices.
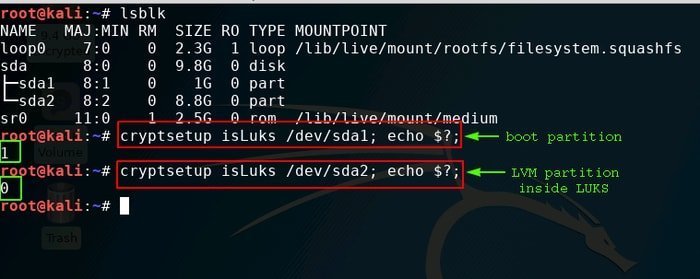
Features of cryptsetup
- An encrypted block device is secured with a specific key, namely, a passphrase key or a key file.
- When cryptsetup takes place in a new dm-crypt device with a LUKS encryption format is called LUKS Format.
- LUKS is the default encryption format required to form a new LUKS device with a default parameter.
- This file encryption tool is essential to generate a filesystem to encrypt data accessible with the device-mapper name.
12. Node.js
Node.js; is open source encryption software that can be used on the Linux platform; it is a run-time environment that applies Javascript code externally to a browser. This utility allows the web developers to encode javascript to write command lines to server-side scripting.
This one is considered the best encryption software and facilitates developers to create dynamic web pages before being used by ordinary users.
It implies; it delegates a javascript everywhere paradigm to unify the web features with a single programming language. Despite having the standard filename extension for javascript code, it necessarily does not refer to the specific files in this regard.
Features of Node.js
- js offers to build a library called crypto which can be used to work cryptographic operations on data.
- With this file encryption tool, the cryptographic operation can be done on buffer, strings, and stream
- The drawback is that if it is installed manually, the crypto library might not be shipped with it.
13. LUKS
It is one of the best disk encryption tools on the Linux platform, which implies Linux Unified Key setup was developed by Clemens Fruhwirth in 2004 by focusing on the core function of Linux. Unlike other disc encryption software that executes various irreconcilable and undocumented formats, LUKS envisages independent platform standards on disc format for using different tools.
Consequently, it works interactively with other programs, enabling all execution password management to be secured and protected in a documented manner. It effectively works on the Linux platform, an updated version of the cryptsetup; that uses dm-crypt to encrypt the dick at the back end.
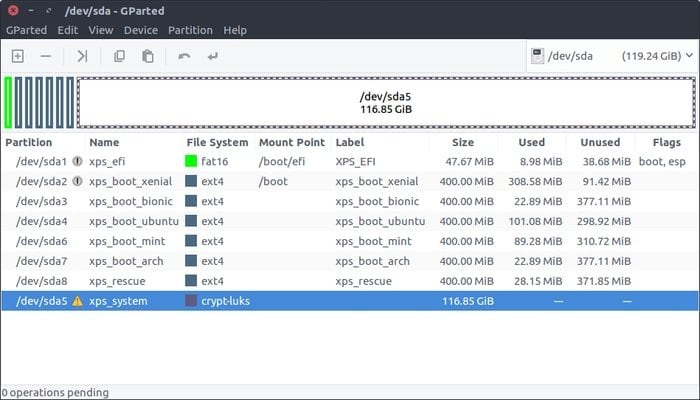
Features of LUKS
- LUKS offers the standard on the Linux platform in its hard disc encryption with a disc format.
- It simultaneously provides compatibility for the distributors and secures user password management.
- All necessary setup is stored in the header of the partition and prompts free information to flow seamlessly.
- This disk encryption software offers the best safeguard on the Linux platform against low entropy attacks.
14. CipherShed
ChiperShed is believed to be the best free disk encryption software on the Linux platform that protects private data and information on a computer. It is the upgraded version of TrueCrypt that facilities immaculate service for the users.
This utility is programmed to create encrypted files and even the entire drive, namely, flash drives and external HDD.
Users do not have to have complicated or sophisticated knowledge to operate it because the step-by-step process needs to be followed to run it.
Being an open source encryption tool, it is available for every user. It is believed that CipherShed is one of the handy and user-friendly encryption after the trucrypt era.
Features of Ciphershed
- Having been encrypted file or disk drive, the encrypted data is mounted via CipherShed that will appear like a regular disc and envisages reading and writing on to on-the-fly.
- This disk encryption software is transparent on the Linux platform and functions effectively too.
- While encryption gets done, the file can be transported or stored elsewhere.
15. AES Crypt
The AES implies Advanced Encryption software is also familiar with its originated name Rijndael. This utility is specified by electronic encryption data released by the National Institute of Standard and technology in the U.S.A. This encryption software is available simultaneously on both sources and application forms.
AES file encryption tool performs distinctly. For instance, the encryption file will be produced with the same name as the core file; however, with a .aes extension.
When aes file gets generated, it does not delete the original file. It is a stable career when users transport or store data and information from one source to another.
Features of AES Crypt
- Substitution –permutation network design principle has been used for this encryption tool what useful for hardware and software.
- AES file encryption software is the extended version of Rijndael, what got a specific block size of 128 bits.
- In this software, round keys have been taken from the cipher key by using Rijndael key schedule.
16. Cryptomator
Cryptomator is a file encryption software that has been developed to protect the cloud file such as Dropbox, google drive, one drive, and other cloud storage services. The local PC is encrypted with this utility, and then it is synchronized with the cloud.
The encryption makes the data readable to the authorized user only, and the attacker gets encountered with its encrypted program. The best feature of this utility is the virtual hard drive that contains all data in a specific folder of the cloud folder. Cryptomator facilitates a virtual hard drive that can be accessed just like the USB flash drive.
Features of Cryptomator
- A passphrase is used in this file encryption tool to secure data from the brute force attack.
- Cryptomator uses advanced encryption standard format to encrypt the data in the cloud.
- Data is protected with this file encryption software in a virtual drive called vaults, encrypted and protected with a passphrase.
- A master key gets generated in the vault folder that secures the data when a folder is created.
17. Boxcryptor
Boxcryptor yields all square user-friendly protected extra layer in the cloud storage that works as a shield to secure data from the attacker. This file encryption tool encrypts files locally on the computer and unleashes protective measures to keep every record safe. Having been optimized for the cloud, all the data is protected and shared among the users.
Files are stored on the server and get synchronized with every connected device. It facilitates getting every file encrypted independently, leaving behind others. Moreover, cloud storage’s typical features, such as selective sync and history, are supported by the boxcrytor facility.
Features of Boxcryptor
- Users necessarily do not need to require the administrator’s right to use this utility.
- It does not require syncing the local file; thus, portable does not depend on the cloud provider sync.
- A portable boxcryptor is available for the Linux 64-bit.
- This file encryption software is the first end-to-end leading technology that secures all files with perfect collaboration.
18. Scramdisk4 Linux
Scramdisk 4 Linux is programmed entirely by focusing on the Linux platform; not necessary to mention how suitable it is to encrypt the file with this file encryption tool. It also offers extra features, namely, a graphical user interface (GUI) that yields and accesses the scramdisck container files.
On the Linux platform, scramdisck encrypts partition on the storage media or hard disc, for example, floppy disc or USB stick, entirely as a device. This scramdisk for Linux is compiled with the kernel driver scramdisk, ko, the GUI scram disc, and the five other command-line utilities.
Features of SD4L
- ScramDisck 4 Linux is a free file encryption tool from the different other subcategories.
- SD4L aims to protect the Linux platform’s driver by encrypting the brute-attacker’s data.
- This file encryption software could change the passphrase by using the change button.
- It is an on-the-fly encryption format that secures an entire file system thoroughly within the regular encrypted file that is called the container.
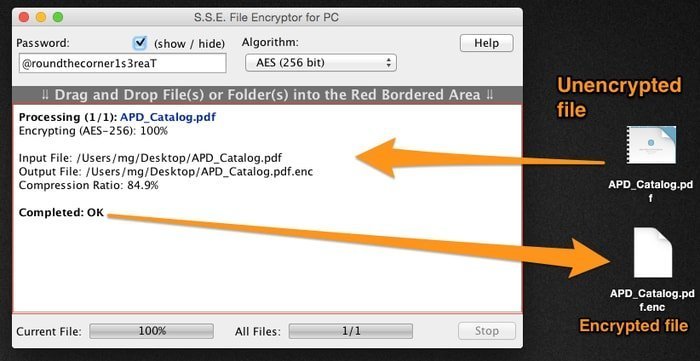
19. S.S.E. File Encryptor
This file encryption software yields you to secure confidential, private, and even the whole folder. Its encryption process is tremendously simple to drag the chosen file into the application window.
Files get encrypted with the robust encryption algorithm, i.e., AES. When the data is instantly encrypted, it generates another encrypted file just like the original one without deleting the core and the .enc extension.
In this process, the original file remains unchanged entirely. Moreover, if required, the original data can be removed, and the encrypted data can be used whenever needed. This encrypted tool is designed with javascript; thus, it performs coherently on the Linux platform.
Features of S.S.E File Encryptor
- This file encryption tool offers the file and text encryption facility; thus, it is called the all-in-one encryption tool.
- A master password is generated within this system that lets all other files and folders be protected.
- This software encrypts all the private, confidential, and entire folders.
- This file encryption software yields to keeping all the text, message, information, and documentation through this encryption system.
20. Gostcrypt
Gostcrypt is one of the best disk encryption software. The latest addition was launched at the end of 2013 and is branded as a fork of the TrueCrypt project. This disk encryption tool envisages going further than ever before happened in this field.
When Snowden revealed millions of classified files from the USA, the world got shaken and since then tried to find out the best possible way to protect the data.
Gostcrypt is one of the products of that concern. Gostcrypt uses 256-bit keys for encryption or decryption. Interestingly, these 256-bit keys are internally divided into eight 32-bit subkeys. In this format, the GOST 28147-89 gets prepared to encrypt or decrypt data and information.
Features of Gostcrypt
- An asymmetric encryption algorithm is used to encrypt data in this disk encryption tool; hence, public and private keys get generated during the encryption.
- It also produces an extension with an encrypted file that makes files well protected.
- During the encryption, gostcrypt surfaces a text message that takes place on the desktop.
Final Thought
To encapsulate the whole article, it would be said that the encryption mentioned above tools are the best disk and file encryption software for the Linux platform. However, it is worth mentioning that TrueCrypt file encryption software has been stopped from publishing the new version; it is still worthwhile for use on the Linux platform.
Users are being requested to leave their comments regarding this article; additionally, if you find this article, information, and links useful, please do not forget to share it.

Tried Cryptomator. Very buggy interface, always locking up, unreliable. On the plus, it installed nicely from a .deb package.
Tried Boxcryptor. Again the “portable” version for Linux gave many bugs, files not uploading properly, screen locking up. Great looking interface, but I think their dev and testing needs much more serious investment. Unreliable.
I gravitated back to VeraCrypt. Yes, the UI look like something from the 1990s, but it is quiet reliable, and for me, I need to know my files are not dissappearing down some Internet black hole somewhere.