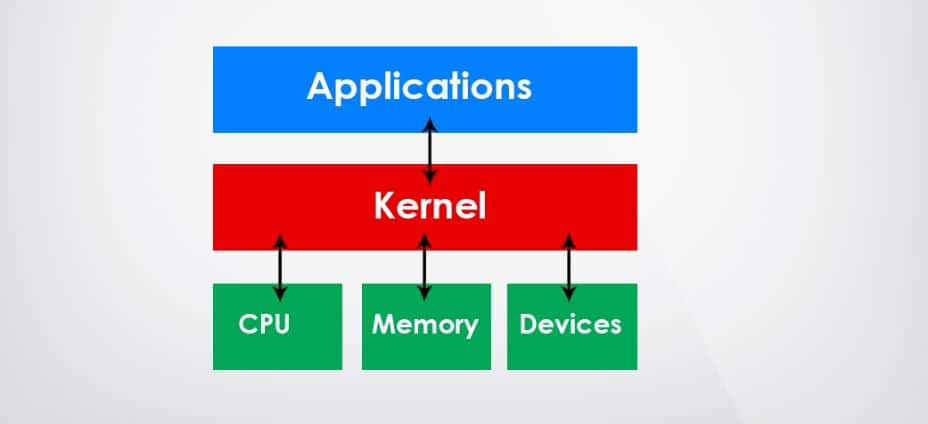
In computer science, the kernel is the soul of an operating system. Linux kernel is designed with very sound architectural knowledge of an Operating system. Linux has mostly three types of the kernel. They are the Monolithic kernel, Microkernel, and the hybrid kernel. Linux has the Monolithic kernel. A monolithic kernel is built for high performance and stability. MicroKernel builds for flexibility and easy implementation. The kernel can access system resources. You can adjust and configure Linux kernel security and settings with the system control tool. In Linux, the system control unit is shortly known as the sysctl.
How the sysctl Works in Linux
Linux file system has a very unique and efficient architectural design to interpret with the core system. Linux kernel configurations are saved inside the /proc/sys directory. The central system control unit or the sysctl tool can be used both as an individual program or as an administrative command tool.
The sysctl can be used to rule the work function of the processor, memory, and network interface card. Moreover, you can make your Linux system more secure and safe by adding your own customized configuration script and commands in the sysctl program. In this post, we will see how to secure sysctl in Linux.
1. Configure the sysctl Settings in Linux
As I mentioned earlier, the sysctl is a kernel tool, so it is a pre-installed tool in Linux. You don’t need to install or overwrite it again. You can just get started with the sysctl command tools. So Let’s get started with the Linux system control tool. To check the current sysctl system staus, run the following terminal command line.
$ sysctl --system
Now you can take action to add your desired configurations inside the system control settings script. You can open the sysctl configuration script using the Nano text editor to add your personal settings. Use the following terminal command to open the script using Nano text editor.
$ sudo nano /etc/sysctl.conf
Inside the sysctl configuration script, you will find some existing default settings. You can leave it as it is, or if you want to make your Linux system more secure, you can add some extra rule and replace the existing configurations with the following settings given below. By editing the sysctl configuration script, you can prevent man-in-the-middle (MITM) attacks, spoof protection, enable TCP/IP cookies, packet forwarding, and log martian packets.
If you are a Linux system administrator or a programmer, you must know that a line of code can be kept as a comment by adding a hash (#) before the line. In sysctl script, the internet protocol forwarding, default redirection settings, and more settings are kept as comments. To enable those settings, you need to make them as uncomment by removing the hash (#) symbol before the line.
2. Control Network Security from sysctl Settings
A few primary and necessary security configuration settings of sysctl are given below so that you can apply them to the sysctl script. To enable IP (Internet Protocol) forwarding, find this syntax #net.ipv4.ip_forward=1, and replace it with the following line given below.
net.ipv4.ip_forward=0
To make your Linux internet connections more secure, you can redirect IP (Internet Protocol) address by changing the value of IPv4 settings from the sysctl script. Find this syntax #net.ipv4.conf.all.send_redirects = 0, and replace it with the following line given below.
net.ipv4.conf.all.send_redirects = 0
Now to make the IP redirection setting as default, add the following line after the previous line.
net.ipv4.conf.default.send_redirects = 0
To accept all redirected IP addresses in your network manager, find this syntax #net.ipv4.conf.all.accept_redirects = 0, and replace it with the following line given below.
net.ipv4.conf.all.accept_redirects = 0
Here is some extra configuration script that you can add to your sysctl settings to ignore incorrect bug reports, set backlog file size, and fix TCP timeout error on your Linux system.
net.ipv4.conf.default.accept_redirects = 0 net.ipv4.icmp_ignore_bogus_error_responses = 1 net.ipv4.tcp_syncookies = 1 net.ipv4.tcp_max_syn_backlog = 2048 net.ipv4.tcp_synack_retries = 3 net.ipv4.netfilter.ip_conntrack_tcp_timeout_syn_recv=45
After you are done with setting the configuration script, save and exit the Nano text editor. Now reload the sysctl tool to activate the changes.
$ sudo sysctl -p
You may now see all the active sysctl rules on your Linux system.
$ sysctl --all
3. Check Kernel Settings
Use the following sysctl shell commands to view the cd-rom info, kernel type, kernel bootloader type, kernel hostname, and other pieces of information of your Linux device. You can also change the kernel hostname of your Linux system using the sysctl tool.
$ sysctl -a $ sysctl -a | grep kernel $ sysctl -a | more
Run the cat command is given below to see the kernel boot UUID and Security-Enhanced Linux (SELinux) status of your system.
$ cat /proc/cmdline
You can check the kernel OS type using the sysctl command from your Linux terminal.
$ sysctl kernel.ostype
Finally, check your Linux kernel configurations by sysctl command.
$ sysctl -a | grep kernel
4. Reset Linux sysctl Settings
As there are plenty of options to change the default values of the sysctl script to make your Linux more secure, there is a slight chance that you may have mismatched the settings and crush your system.
As long as the Linux kernel is running, it doesn’t preserve the default values when a root user changes the values. So, if you don’t want to damage your system, please copy and paste your default sysctl values into notepad so that you can replace your default setting in case of an emergency.
Here is an alternate way that you can use to restore the sysctl settings on your Linux device. If you are using a Ubuntu machine, find another Ubuntu machine and get the default system control (sysctl) configuration script from it. Then copy and replace the script to your device.
Finally, Insights
In general, the sysclt tool can be used to configure the Linux kernel settings and parameters, but it has an extensive range of usages. This tool can be used to compare the stability and adaptability between different versions of the kernel. Though there are some other tools and programs are available to compare the stability of different kernels. Still, very often, they may not show the perfect result where the sysctl is a very reliable tool to measure and configure the kernel parameters.
In this entire post, I have illustrated the basic concept of the Linux kernel and demonstrated how to secure your Linux system with the sysctl tool. If you find this post useful and informative, please share this post with your friends. You can write down your valuable opinions in the comment segment.
I read this as “harden your server buy removing the # before the setting to turn it on or off”. No meaning or description as to what these settings actually do.
Would be beneficial if you explained why someone might want to change a particular setting i.e. the reason for changing the setting.